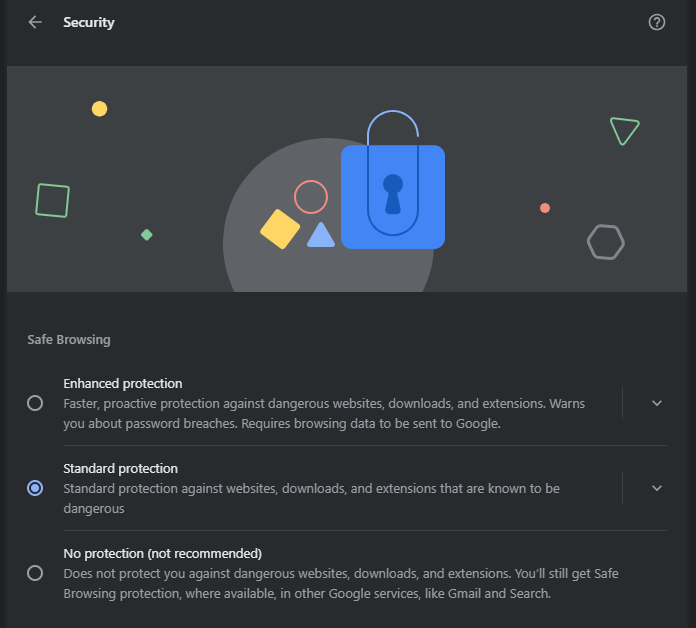
If your computer is going to dip its toe in the internet ocean, you need protection. There are hazards everywhere, and nothing is sacred on the wretched worrisome web. But antivirus isn’t enough. Whether you are using Microsoft’s free Windows Defender Antivirus, or shelling out big bucks for Snotron McAffeinated 420 Ultra SmartWare Gigaplex Security Suite 2025 Excruciating Edition, you need more. No antivirus is going to keep you 100% safe from the hazards of the internet.
After your antivirus is squared away, you need an ad-blocker. This is software that suppresses or blocks advertisements from ever appearing as you surf the web. And you really need to be blocking ads, on (almost) all websites. They can be dangerous no matter where you go.
Irresponsibility
Websites everywhere look to make a buck through advertising. But they often don’t want the tedium of finding advertisers, collecting ads and payment and other managerial minutiae. It’s much easier for a company to hand that task off to ad firms, who will place and rotate ads on designated places on their website.
But that leads to trouble. If the ad firm doesn’t vet their customers well, or if they suffer a data breach, or if they just don’t care, then you wind up with this nonsense:
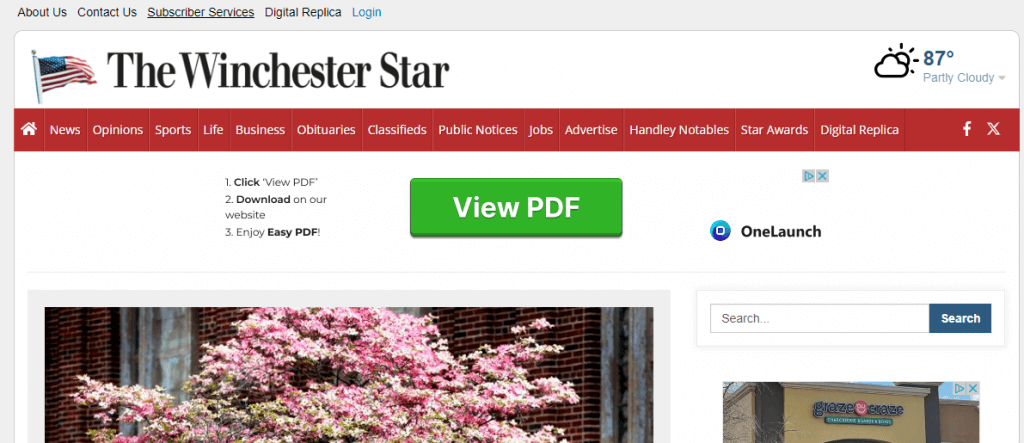
To be clear: This screencap is taken (today!) from a Valley newspaper’s website, that most people in the region visit for local news. Directly under their masthead is a large banner ad that will lead people to two different types of undesirable software downloads. I cannot tell you how many computers I have cleaned of OneLaunch this year. And EasyPDF is a well-known search hijacker. Some people are going to ignore that junk. Other people are going to click on it and foul up their computers and have to call a professional to clean things up.
As much as I like to earn my pay, this isn’t right. This is irresponsible, although it is debatable whether the fault lay with the newspaper or the ad agency they’ve hired. Whomever we should wag the finger at, they are unlikely to be sympathetic or helpful when it comes to fixing your computer. And this sort of thing happens frequently, on many of the mainstream websites you visit.
Hence my stance: You need an ad-blocker! An ad-blocker is the second layer of protection for your computer, after your antivirus.
Ad-Blocking Options
There are a lot of options for blocking ads, and they usually do not come from your antivirus vendor. And there are even scammy and spammy ad-blockers out there, so let me suggest some that I know to be legitimate and safe:
AdBlockPlus: I’ve used this browser extension for years and it has been consistent and solid since its inception.
uBlock Origin: Also a quality ad-blocker extension, but this one is fairly unique, as it does not ever ask for money, even a donation.
The Brave web browser: Brave is not an ad-blocker, it is an entire web browser with ad-blocking, baked in. It is a modified version of Google Chrome, with lots of privacy and other protections added into the mix.
I should mention it is best to pick only one ad-blocking solution and run with it. If you need to change, remove one before adding another. Multiple ad-blocking softwares can conflict or cause system slowness.
A Final Caveat
Using an ad-blocker may change your life. If you haven’t used one before and this is your first time, you may be amazed at how much more pleasant the internet becomes, with all of that chaff eliminated from your news, your webmail, your shopping websites…
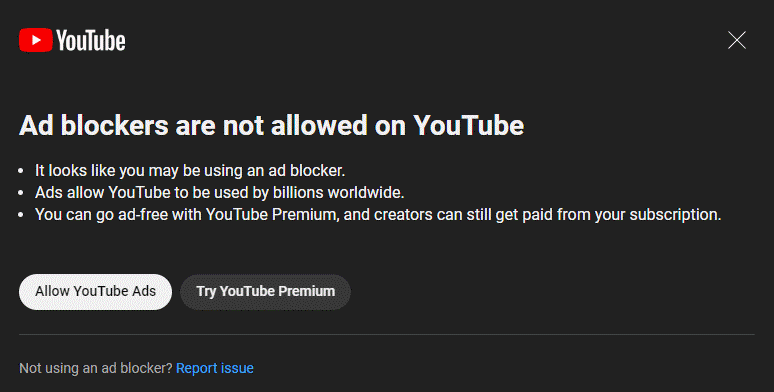
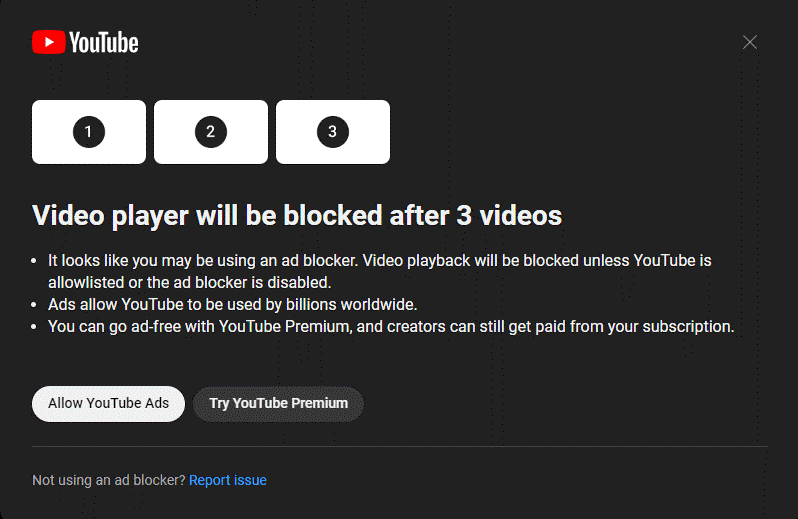
But some websites don’t like that you are running an ad-blocker. They can tell. Those sites may pop-up messages when you visit, exhorting you to disable your ad-blocker, so that “we may continue to rake in those sweet sweet advertising dollars!” Most of these messages you may safely ignore, but a few websites are a bit more rigid than others. They may prevent you from using the website, until you turn off your ad-blocker. In those instances, you have a choice:
A) Disable your ad-blocker for that one website. Usually, you would find the icon for your ad-blocker, click it and then toggle it off. After you refresh the website, ads will show for that one webpage, but the ad-blocker will still function everywhere else you surf.
B) Don’t visit that website. Just leave. If they won’t respect your need for computer security, then perhaps they don’t need your patronage.