Miners used to bring canaries with them deep underground, to help detect dangerous gases. If the bird perished, the humans knew to retreat before they too suffered harm. Nowadays, the canary-in-a-coalmine concept extends to other type of alerts & security “tripwires”, such as Thinkst‘s Canary Tokens.
Offered as a free service, this website allows anyone to generate a canary token and make immediate use of it. Now, many of the token options are beyond my ken, and I won’t embarrass myself, trying to explain them. But there are a few options here that are accessible & usable by most computer users. If you click the first drop-down menu on their token page, consider the options for Microsoft Word Document, Microsoft Excel Document and Adobe Reader PDF Document.
Creating a Token
Select the token document type, fill in an email address and the notes field below. Here’s an example:
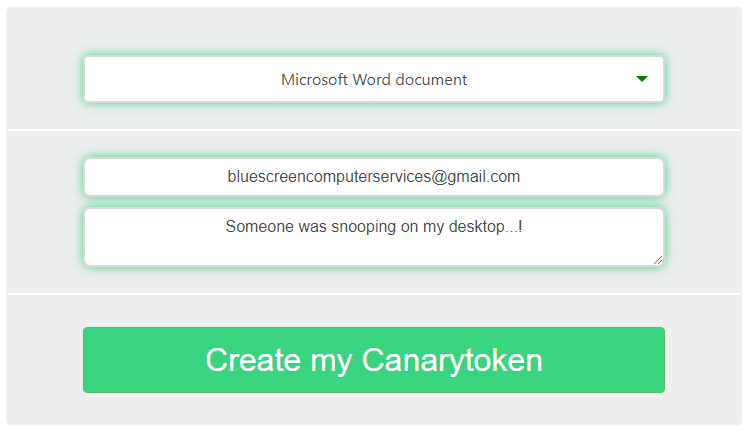
Click the Create button and then the Download button on the next page. For the pictured example, you’ll now have a Word doc with a weird name to it. And now you can plant it somewhere to test your security.
Examples of Use
With a Word, Excel or PDF file token, you might just place the file on your computer’s desktop, or some other conspicuous place. Rename the file to be PASSWORDS.docx or InvestmentAccounts.pdf and then wait. If someone comes snooping while you are away from your system, you’ll get an email as soon as the file is opened.
If you’re an employer, you might test your staff’s security savvy by emailing out a harmless test phishing message. Send them a suspicious email with a token attachment. If they aren’t fooled, and they report the message to you as a fake, great! If they trust the email and open the attachment, you’ll get email receipt(s) about it. Depending on the results, you might follow-up with some internet safety training.
If you are worried that your email is being intercepted, then attach the token file to a new message and send it to yourself. When you receive your own email, let it set and do not open the attachment yourself. If you later get a canary token alert, that will help to prove that the attachment was opened by someone else.
Final Comments
I’m just scratching the surface with what canary tokens can do. If you work in web design, infosec, or other tech fields, the other listed options for canary tokens may make a lot of sense to you. They can help you figure out if/when your database has been stolen or misused, when a website has been intruded upon, and more.
Also, please appreciate that this tool is not specific to any operating system. You can use canary tokens on virtually any machine you have control over.


Leave a Reply