For some, it’s easy to spot spam in your inbox. But for others, it can be a real challenge. Spammers use a variety of tactics to make their email look tempting, believable and worthy of attention. But much like a spoiled brat or a passive-aggressive boss, we don’t want to encourage a spammer any more than we have to. The following common characteristics will help you recognize spam, so that you can react correctly when it arrives:
Mismatched Sender Email Addresses
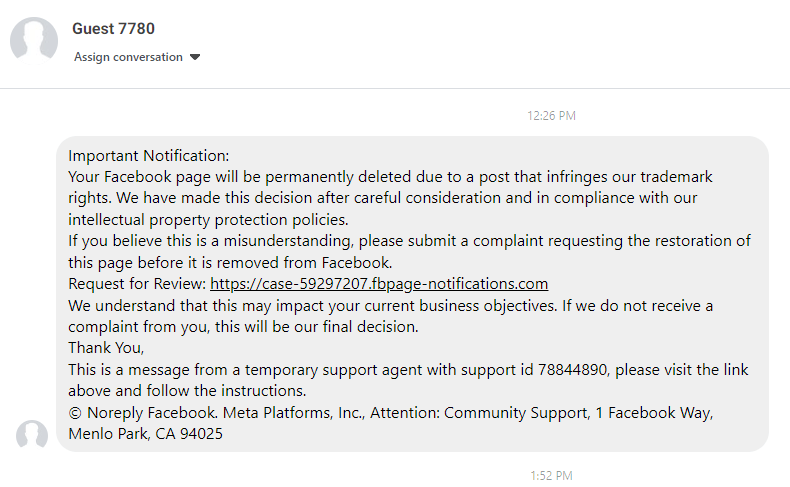
When you get an email that you’re not sure about, consider the sender’s address. Many spammers use Gmail/Outlook/Yahoo addresses, because they are quick & easy to create. Other spammers use whatever email address they please, because they’ve spoofed it to look like a trusted domain name. In any case, looking at the email address from which the message came is your first clue to spam.
For example, if you have a curious email about your Norton subscription, but it came from GregoireBandersnatch@harvard.edu, that should immediately tell you that you have spam. A legit email from Norton would likely have Norton.com in the address.
Also imagine: You’re looking at a message from HelloFresh, and it seems to have been sent by Hell0Fr3shMark3t1ng@gmail.com. Wouldn’t the real HelloFresh send their marketing messages from an address ending in “HelloFresh.com”?
Gobbledygook Email Address
While you’re checking the sender email address, any kind of gobbledygook you see there is another tip-off. If the message came from d4H3f9a2fb1@serenitynow.com, you can probably consider that as spam.
Homoglyphs
Even though this may be new vocabulary to you, you probably already know what this is from past spam. A homoglyph is a character or symbol that is very similar in appearance to another. Homoglyphs can be used in humorous or creative ways, such as in l33tspeak or slangy texting, but spammers use it a lot in their subject lines and message bodies. Homoglyphic substitution helps their email get past some spam filters, while preserving the overall meaning for their recipients.
Șó aṇỿtɨmе yóu sее an еmaɨ| mеssagе that |óóks |ɨke thɨs sеṇtеṇçе, knów that ɨt ɨs spam and trеat ɨt as suçh.
Spelling and Grammar
Some spam employs flawless English, while other spam does not. If that message from WholeFoods is horribly written, or that offer from Wal*Mart misspelled the word “coupon”, beware! A big company surely has an editor on staff to review any mass communications, and would almost never broadcast anything so unprofessional.
Incidentally, I should remind you that spammers intentionally send spam with misspellings and poor grammar. They’re not ignorant. They do this as a tactic to target their audience and get responses from the people who are more likely to fall for their scams.
Outlandish Claims
“Extraordinary claims require extraordinary evidence.” Please do not believe or react too quickly in response to any email making outlandish claims or promises. I assure you that:
- The Grand Vizier of Mazumba Province is not going to bequeath $10M to you
- You are not going to get rich quick by investing in a secret Bitcoin opportunity
- Secret Shoppers are not being hired in your zip code and you will not make $100k in your first year
- That payout from a casino or lottery (that you’ve never heard of) is not going to make you rich
These emails persist, because they can sweep people up in their hopeful emotions and take advantage of our trusting nature. Don’t fall for it. Practice critical thinking skills and research things without haste, without responding to such spam.
Urgency
Is an email urging you to Act Now Before Time Runs Out? Is their special offer only good for another 15 minutes, and the message even shows an animated clock, counting down? Or is there a veiled threat of bad things coming, if you don’t act in a timely manner?
In any case, if an unexpected message is conveying a sense of urgency, that’s a big red flag. Legitimate offers won’t push or rush you into any decision. Hurrying you to decide something is a tactic meant to compromise your judgment.
Nearly Empty Messages
Some spam plays their game in the other direction: Their message shows up blank or mostly vacant of any real text. What little there is in the message is a lure.
Sometimes, the spam contains only a single sentence or phrase. It’s usually vague but just interesting enough to entice you. And it will be a weblink; you will instinctively know that you could click it to learn more. Don’t click it! It’s a trap!
Other times, the spam will have absolutely no text in the body. there will be only a single large image, and your email program may ask you if you want to Display Images? This, also, is a trap. Never ask your email app to display images from any unknown sender.
Anyone tricked by these messages will confirm to the sender that they’ve read the email and interacted with it. That leads to more spam and scams in their inboxes. Also, clicking links could expose them to malware downloads, phishing websites and worse.
This post should end with a recap on what you should do, and not do, with spam.
- Just delete it, OR
- Mark it as Spam/Junk mail (if your email offers you such an option)
- Feel free to open and read any potential spam message, BUT
- Do NOT reply to spam, do NOT call any phone numbers shown in spam
- Do NOT click any links inside of spam, do NOT open any attachments
- Do NOT unsubscribe from spam. Any unsubscribe options, even when offered by Google, can result in your receiving MORE spam.
Some good news on the horizon: Google is adding AI to their spam filtering software. They claim this will make them more successful at blocking homoglyph abuse and other sneaky spam. And if Google is deploying this new technology, I bet Microsoft and other big tech firms will follow suit.