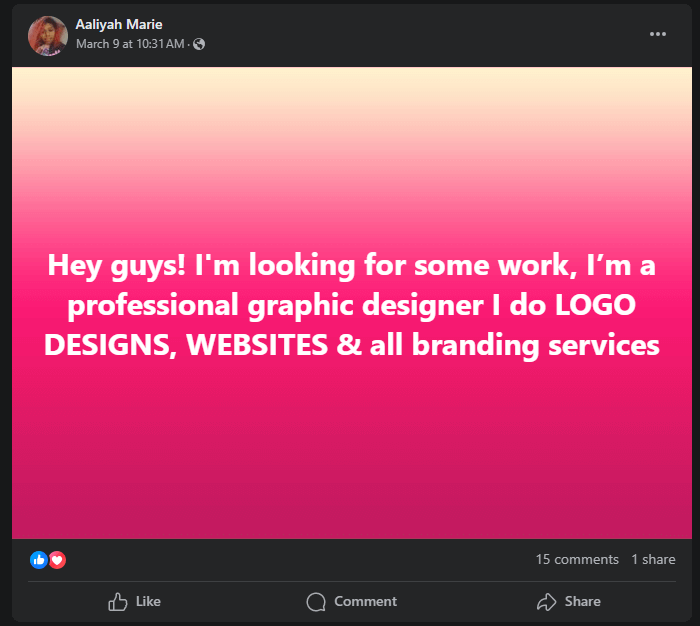
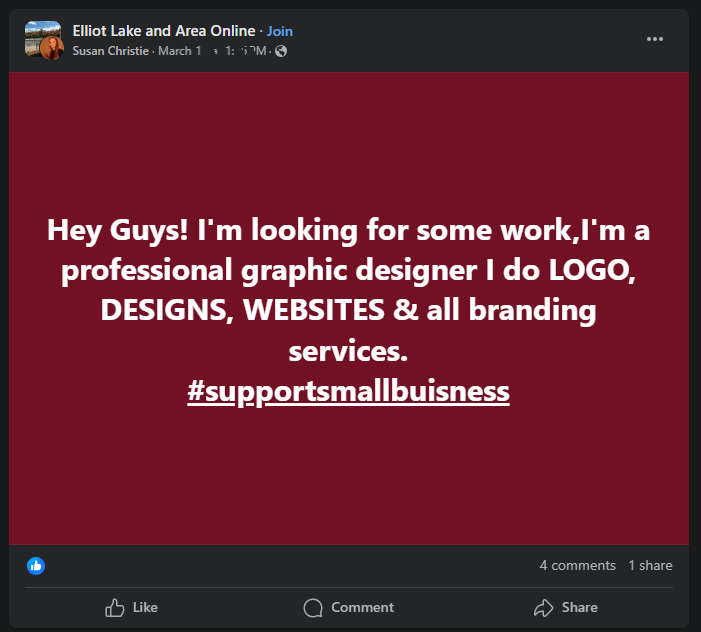
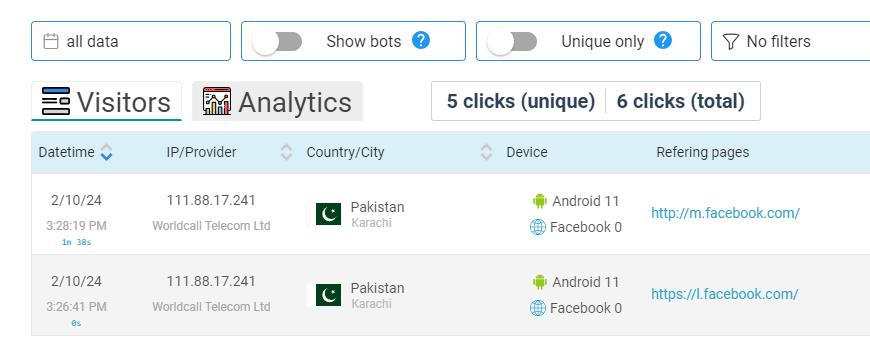
Someone recently asked about a business page on Facebook: “Hey, is this company legitimate? Am I going to be scammed by them?” I took a quick look and quickly saw the danger. Please check out the details below to become better at spotting a fake company on Facebook.
The Basics
The page that I was reviewing today was Asphalt Specialist & Driveway Maintenance. In case Facebook removes that page, I’ll also link to an archived copy of that page, for anyone to review.
On the surface, this looks like a perfectly ordinary business profile. I see a local phone number and address, plenty of good reviews, and solid English used on the posts and descriptions. No obvious red flags for the casual observer!
Digging In
On this profile, I started by clicking About and then Page Transparency. This asphalt company showed:

From this, we see that the page was created only 5 months ago, and is managed by people in the US… and Spain? A rural West Virginia paving company with a connection to someone across the ocean?
Checking the Basic Contact Info
Next, I copied the phone number and threw it into a Google search, and also into DuckDuckGo. And these searches immediately connect with paving and sealcoating services. But the results link to companies with different names. And different locations. Nothing matches up with the contact info on the Facebook profile.
So I regarded the address. Copied & pasted it into Google Maps, Bing Maps and Mapquest (yes, they’re still around!). Each mapping service quickly put a pin down and offered directions to that location. But none of them mentioned a business at that pin. And something’s seemed off, satellite imagery didn’t show buildings right at the pin drop.
So I got a bit analysis-retentive. I learned that the address was in Berkeley County, WV. Most counties have a handy GIS/mapping website for their properties, and Berkeley County’s was easy to find. It wasn’t the easiest to use, but I persevered and found that the address shown on Facebook doesn’t exist.
Digging Deeper
I returned to the Facebook profile to admire their posts and photos. The logo looked like an AI creation, but I see that happening more and more with real businesses, so I moved on. Browsing through the photos, I picked a fairly unique one, showing a man finishing a driveway job. I right-clicked that photo and chose “Search Image with Google”.
Google quickly popped out a side panel, showing similar photos and one exact match. The exact match was on a different paving company’s page. A company in Michigan.
I repeated this with a different photo on their Facebook profile. And that photo tracked back to a Craigslist post:

It was starting to look like their images were all copied from other websites. A business that’s copying images, as well as contact info? Definitely shady, enough for me to be sure about this outfit and turn them in to Facebook. But I found one more bit of copy-fraud:
The Glowing Reviews
This profile showed a high rating, from the get-go: 4.9 Stars, from 57 reviews! Pretty good for a page that’s not only a year old. And most of the reviews are wordy and very detailed and using proper English. But the devil is in the details.
Scrolling through these reviews, I soon noticed repetition. Different people had posted the exact same verbiage as each other. Next, I clicked through to look at these people posting the reviews. Most of them seemed off. They appeared to be posting various glowing reviews for a wide variety of services. I started to wonder if they were sock puppet accounts. And that perhaps all of the companies they were reviewing were bogus, like our Asphalt fakers.
By the way, this fake review technique has a name: Astroturfing. It’s sort of the opposite of review bombing.
Case Closed
I’m convinced that this Asphalt profile smells of fraud, so I did report it to Facebook. If somehow this is a real business, then they’ve been dealing with fraudsters to get reviews and other people’s photos on their profile. Please be ready to report anything shady to Facebook… even though it doesn’t do much.
Facebook is like the wild wild west. There’s a pretense of law & order, but it’s just too big to police. Or perhaps they don’t care to. Keep in mind that this scammy page is actually paying Meta to run their ads, while you are using Facebook for free. In other words: