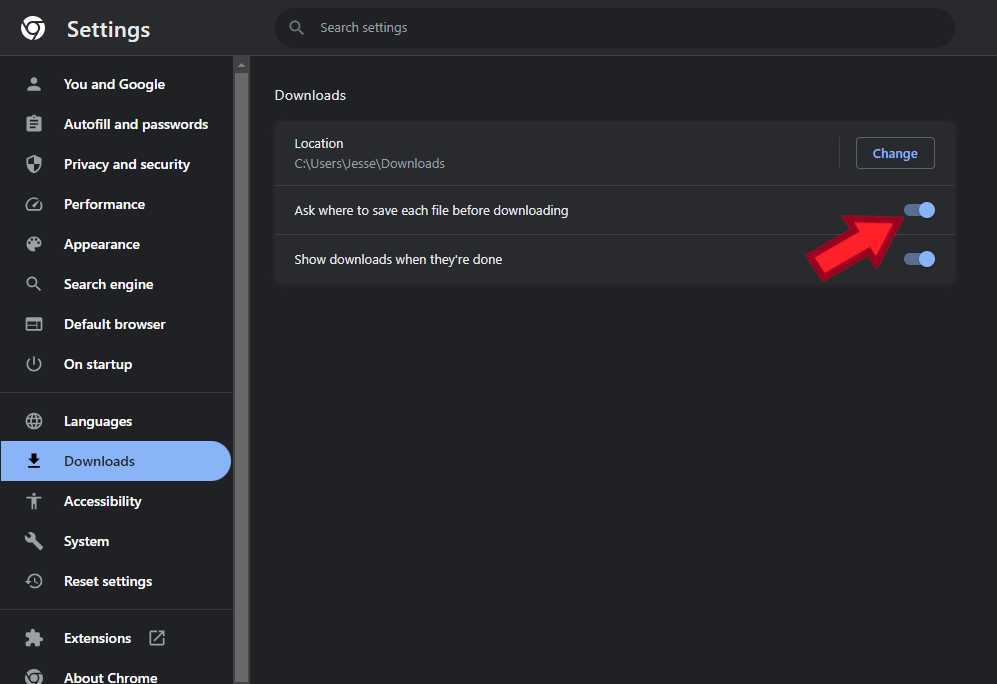
Everyone is free to choose what web browser to use on their computer. Many people use Edge or Safari, because it came as part of the operating system on the computer. Others opt for Chrome or Firefox. But what is worrisome and worth warning about is the use of rogue Chromium browsers. I hope I can teach you what these are, so you can recognize and avoid these.
Let me clearly state: Google Chrome is a good browser to use. If you use Google Chrome, please continue to do so! Chromium browsers are different. A Chromium browser is essentially a modified version of Chrome that has different abilities or behaviors. Many of these tweaks can lead to harm.
Examples of Rogue Chromium Browsers
The first Chromium browser that spread to average computer users was labeled Chromium, and had a blue-tinted icon, very similar to the classic Google Chrome icon.
This open-source version of Chrome was meant to be used by developers, programmers and other technical experts. To my eye, it really stands out when I find it on a layperson’s computer, and is often my first clue that I’m going to find other unwanted software…
Wave Browser is an example of a modern-day rogue Chromium browser. It is polished, has a classy logo/icon, and appears to be professional and fast to open. Those who use this may feel right at home, because its menus and behavior closely resemble Google Chrome. I’ll get to the devil in the details, though, in the next section.
OneLaunch is another rogue to watch out for. But this one is easier to spot, as it comes with a special bar that permanently eats up the top half-inch of your screen. OneLaunch will function as well as any other browser, but let me describe more of what’s under the hood here:
Detriments of Using a Rogue Browser
Sketchy Search Engine: These browsers often steer their users into using a modified version of the Yahoo search engine. This engine is not anything I would ever use. It’s been altered to include more ads and paid placement than the usual Yahoo engine. Many of the top results you get from this are promotions, malicious links and phishing sites.
I searched for “Xfinity phone number” in a variety of search engines, just now. Google, Bing, DuckDuckGo all returned solid results and the safe trustworthy phone number for Comcast. Yahoo.com also gave me good info. But when I use Onelaunch and WaveBrowser to do the same search, the results were riddled with ads and websites I would never want to visit. I can see this behavior leading some users to scams and false information and phishing websites.
Modified Start Page: When I test these rogues out, I notice the Start Page has been customized, to show a lot of strange things. Some are salacious news articles. Others are gross advertorials about health conditions. And even others are lures to bogus antivirus messages.
Eating Up Screen Real-Estate: Some of these browsers take a lot of liberty with your computer. OneLaunch installs a bar of icons across the top of the computer, and it remains up there, even after you close the browser!
Empty Promises: In some of these browsers, I see them boast that they offer Camera Privacy and better ad-blocking. I just can’t even with this nonsense. People desiring camera privacy simply turn off their camera. Close the shutter on their camera. Disconnect their camera. Slap a Band-Aid over their camera! Whatever your concerns might be about webcam surveillance, you should not be turning to a mystery app to solve them.
Constant Nags: These browsers may have various popups, trying to convince you to set them as your Default Browser, try out their extra products and more.
Who Really Makes These Browsers?: It can be hard to tell who’s behind these programs. I went looking into Wave Browser’s pedigree. It’s created by a company called Wavesor. That turns out to be the trade name for Polarity Technologies. Which is a subsidiary for Genimous Technology, a Chinese firm that has been investigated and criticized by our government officials.
What Else Came With This Program?: These rogue browser are downloaded and installed, often without the computer user understanding how or even when it happened! They can be sneaky like that. And if this app showed up unexpectedly, chances are good that they came with other potentially unwanted programs. I often find other adware to remove when I service computers with rogue browsers on them.
Moving Back to a Mainstream Browser
The good news is that if you want to reverse course and go back to your previous browser, that should be easy. Uninstall the rogue app, and your other browser(s) should still be there. These rogues don’t harm or delete anything from your system.
After that, you may want to run a few scans on the system. There could be some junkware, separate from the browser, that needs to go. Your antivirus is just the first tool to consider. I like to run specific tools, like ADWCleaner or Norton Power Eraser, to look for hidden nasties.
If you are struggling with this cleanup and feel in-over-your-head, please know that I deal with this everyday, and can help you in restoring things. Reach out to me if you feel like your computer is still acting “off”, or if any computer task is “above your paygrade.”