If you have a Dell computer, you may have recently received an email notification of a data breach. Millions of customer records were recently stolen from Dell. Here’s what you need to know about the Dell 2024 Data Breach:
What Was Stolen
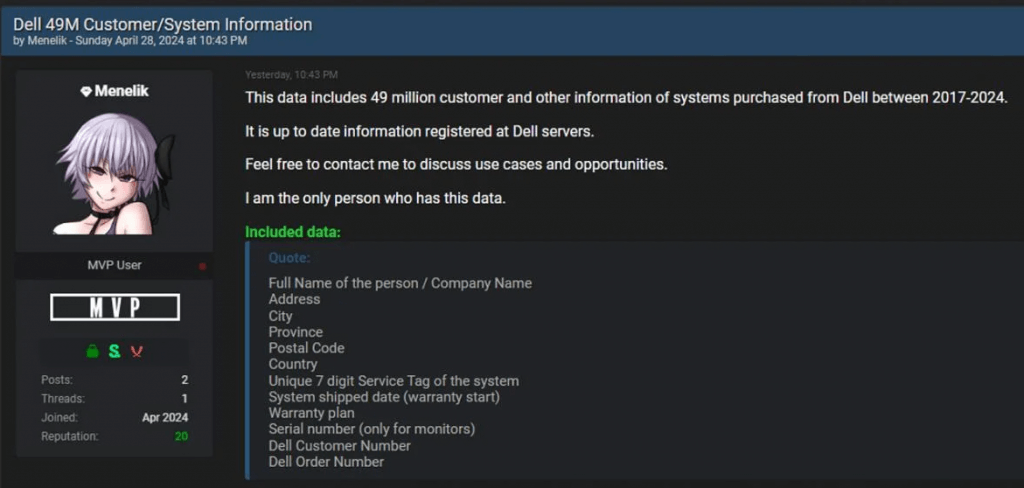
49 million customer records walked out the door. Each record may contain:
- Purchaser’s Full Name
- Physical Address
- Unique Service Tag from the computer/hardware
- System Ship Date
- Warranty Plan Details
- Serial Number (for monitors)
- Dell Customer Number
- Order Number
At this time, Dell claims that no payment info or phone numbers were taken. We can be grateful that there’s no worry about any financial accounts being invaded. But this breach is still a big deal, far bigger than Dell is letting on in their blanket email. The potential for phishing scams, using this stolen info, is high.
What To Expect
We’ve been through this before. It is generally known in the tech community that Dell has had other data breaches, and just not fessed up about them. How is that, you ask? Over the past several years, various Dell scams have been reported on or discussed, and those scammers used inside info, like Dell Service Tags and PII. The customer data they used was specific enough to have only come from Dell’s records.
These scams work well, and here’s an example of how it plays out:
Joe Scammer runs some quick searches against pubic information databases, and finds phone numbers to go with the names and addresses he’s holding. Then he starts cold-calling those numbers, with a plausible story.
“Hello, Ms. Vanderbluth! I am John Snordwrangler from Dell and I see that your Inspiron 3450 is overdue for a BIOS security update. If your service tag is BXT459A54, then I am authorized to perform this fix, free of charge for you! Do you have 2 minutes for me to remote-in and secure your system?”
This is often their schtick. And it is very believable, because the scammer already has all the answers. He’s not asking for sensitive info, he already has it, and many people would not think twice about saying Yes to a free fix. But anyone duped by this scheme will soon be taken for a horrible ride and bilked out of significant money. Or have their computer ruined after they refuse to pay up.
Based on past scam attempts, we might expect these to come via phone calls, email messages and even postal mail! Yes, you might even get a letter in the mail; it has happened before in other schemes.
How to Protect Yourself
This is a tough one to guard against. Again, the scammers will come armed with a lot of your personal information. They may employ the Dell logo on their printed materials. They have the ability to falsify their CallerID. Their email address may be spoofed to show “support@dell.com” or the like.
I have to prescribe extreme dubiousness for any Dell communications you receive. Maybe this should also apply to any unexpected contact from big tech companies. If you didn’t initiate that surprise call or email, mistrust is a good first option.
But there is always the slight chance that you will receive a legitimate Dell notice. So we’ll want to be suspicious but not impolite. Don’t respond to any Dell emails directly. Don’t interact with a Dell rep who called you on the phone. Never dial a number shown in an unexpected email.
If Dell is asking you to take any particular action, end the call or step away from that particular email. Next, you are safe to reach out to Dell, using trusted means, as shown on their website. The various phone numbers and chat methods on that site are safe. Using them will help you verify a real request, as well as reveal a phishing attempt.
Please also discuss anything strange with your friends, family or other trusted people. Remember: scams reveal themselves and fall apart when you talk about them with others!
Also, Dell asks that you report their impersonators to them. They have a page for reporting phone scams, and you are welcome to forward phishing emails to security@dell.com .