Remote control scams are alive and well in 2023. I blogged about this just a year ago, but this is important enough to go over again.
A remote control scam is where someone is out to steal your money, and they use remote control software to get into your computer. Once they have access to your system, they’ll push further into your finances (and your consciousness) to take as much as they can. Some of these bad guys are aiming for a quick $300. But this year, I’m seeing where they aim higher. In the last month, I’ve spoken with victims who have lost $30,000, $75,000, and more than $100,000 to these cybercriminals.
What makes these scams so dangerous, though, is that there is nothing you can put on your computer to protect against them. There is no virus to guard against. Your computer is not being infected or hacked. It’s largely a social-engineering operation, where the victim’s brain is the target. If the crook gets inside your head, then they will win. So please be knowledgeable about how remote control scams work, so that you don’t become a victim someday.
How These Scams Begin
A remote control scam begins over a phone call. That call starts in various ways:
- A unexpected notice pops-up on your screen. It claims you are being hacked or infected with many viruses. Or it may accuse you of viewing illegal adult content and threaten you with fines or arrest. A robo-voice warning may blare out of your speakers, and urge you to dial a particular phone number. These pop-ups are often difficult or impossible to close.
- You receive a robo-call. The recording tells you that there is a problem with your computer or online account, and you should press 1 to be connected with an agent now!
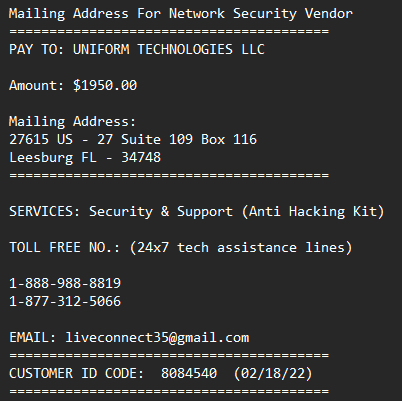
- An email announces that a charge is pending for something you didn’t buy. Something like a Norton renewal, Geek Squad payment, or an expensive app from the Apple Store. And at the bottom of the email, a phone number is offered to you if you wish to dispute the charge.
These alerts almost always drop a big name: Microsoft, Paypal, Amazon, Apple, etc. But that big tech company is not responsible for the urgent notice. You’re being lied to by an impostor. The scammers are just looking to get that phone call started, by stealing and using a respected name and logo!
Getting Inside Your Head
Once an active scam phone call begins, the cybercrook gets to work immediately. And their work is akin to hypnotism. They tell an urgent story, using very convincing jargon and details, in order to get your cooperation.
There are so many stories I can hardly remember them all:
- Hackers are attacking your PC right now!
- No worries, I can get you a refund for that charge.
- I see that your computer is running slowly, and I will fix it for free.
- We overcharged you in the past and would like to compensate you as an apology.
- You have not paid these back taxes and officers are coming to arrest you in less than an hour.
If they get inside your head, the next step is to see if they can get inside the computer (or mobile device). They guide the victim to install a small program for this. And often, the victim hardly realizes what’s going on, due to the stress & panic of the situation.
If You Give a Crook Your Mousie…
These bad guys use the same remote control tools that all the good guys use. They just need to convince their mark to install one before the scam can progress. Here are some examples:
- The crook emails a link to the victim, for downloading their “helper” app. They instruct on how to click the link and then to click Yes on any prompt while the program loads.
- The scammer asks the victim to open Quick Support from the Windows Start Menu, and they ask for the access code on its screen.
- A bad guy explains how to open a Run window. He then dictates a website to type in, something like www.ammyy.com or https://get.teamviewer.com .
- The criminal tells how to use the app store on the phone to get an inspection app. But once the app is opened on the phone, it turns out to allow remote access.
Anyone who follows these kinds of steps will permit a scammer full control over the computer. It is the same as when I connect to your computers to fix them. The cyber criminal will see the screen and be able to mouse around on the system. But they aren’t there to fix anything. Instead, they’re fixing to invade some bank accounts!
Further Convincing Details
Once aboard the computer, the bad guys often “get right to work”, running scans and opening lots of windows. They may show off a complicated Control Panel to show the thousands of errors on the system. Or launch a DOS window that is covered in IP addresses of the hackers targeting the system. They also can place lots of new and curious icons on the desktop:

Whatever they demonstrate is just computer theater. The goal at this stage is to overwhelm and impress the victim, to get them to fall in line. They are “tenderizing the meat.” The crook really wants to be sure that they’ll get full cooperation on the next step of the plan.
Step 3: Profit
If the scammer has gotten this far, they will now start the financial part of the scheme. Some scammers still ask for gift cards, but the greedier criminals want to see the online bank accounts. They know it’ll net them more money. So they insist that the victim go to their banking website and login, with these types of stories:
- I will be happy to refund you the $500 fee, if you can just show me what account number to transfer it to.
- We must safeguard your savings before the hackers get to it. They have almost gotten your money, but we can move it to a safe government holding account before they hack you!
- You can satisfy your debt with a quick transfer and I can show you how to do it through your bank’s billpay.
These criminals usually don’t care what your bank password is. They typically ignore your bank account numbers. They just want to see your balance. They want to see what the jackpot amount is, and their next scheme adjusts accordingly, to drain your account. One possible scenario:
The thief spots $500 in the checking account and $50,000 in the savings, They offer to refund the fake Norton charges to the checking. “We will give you your $400 back to you right now!”. But after they initiate a transfer, the bank account will refresh and show a $40,000 incoming deposit. The scammer will get angry and loud, claiming, “You mistyped it! You messed it up and took $40,000 from me! I will lose my job for this! I will call the police on you, unless you send me back that money!” And then he will attempt to wire transfer $40,000 out of the savings account to … some other account that he controls.
Here’s another far-fetched story:
The crook sees $20,000 in checking and $80,000 in savings. They say, “OK, look, we can save your money, but we have to move it all into your checking account. The hacker is attacking your savings account” After a quick money shuffle, the checking account holds $100,000. “Oh no, the scammers noticed what I did, now they are hacking after your checking account! We will have to move all your money to a protective FBI account. If we don’t, the scammers will take your money in the next 15 minutes. I can see that they have almost hacked your Bank of America security. Quickly now! We can bring back all of your money after the scammers are defeated!”
This is it. If the scammer has gotten this far, they’ve just won the lottery. The small fortune in American Dollars they’ve just grabbed will convert to a large fortune in their country’s currency.
If they have anything else to do with their victim at this point, it will be to buy for time. They may have other stories now, to calm the victim, to get the victim to relax and just wait a few days. This is to give them time to transfer and hide the money, to make it harder to for that money to be clawed back when the fraud is detected.
If You Have Lost Money To This Scam
After the scam and phone call ends, the hypnotism will fade away and the truth will dawn. At this point, you’ve got to act fast, to get a tourniquet on the situation:
- Contact your banking institution to let them know you may have been scammed. Do NOT wait until the morning, call any and every number you have for them, until you reach a live human. Describe the entire scam-process to them, and they will know what you are talking about. Follow all of their instructions to a tee, to protect your account and seek recovery of your money. The sooner you contact your bank, the greater your chances of recovering your money!
- Disable or uninstall the remote control software used by the bad guys. If you don’t know how to do this, turn off the computer and seek legitimate computer help!
- Change your online banking password (your bank may help you with this when you contact them). Change the passwords to any sites you logged into while the bad guys were connected to your system. Change as many passwords as it takes to get your peace of mind back.
Final Notes & Commentary
When I teach people about these scams, a frequent comment I hear is “Boy, how stupid do you have to be to fall for this?” Let go of that sentiment right now. Scammers can rob people, regardless of intelligence or education level. I have helped so many people recover from these crimes, and the victims come from all walks of life. Some are business owners. Others are teachers. Many have gone to college and have Dr. before their names or many letters after their names. Let’s not victim-shame or victim-blame. We should instead focus on how skilled the criminals are at their game. Some of them truly are world-class hypnotists. Recognizing them as a serious enemy is a better mindset.
Big tech companies are not going to call you out of the blue with an unexpected crisis. It’s always a scam. If you still have doubts, talk to someone else before taking action. Call a friend or a computer tech or a family member. Only call phone numbers that you can trust 100%, like those printed on your billing statements or found at GetHuman.
Antivirus software defeats viruses. Ad-blockers stop malicious ads. Firewalls defends against hackers and malware. But as I mentioned at the start, this type of scam belongs to none of those threat groups. It doesn’t matter if you have a PC, a a Chromebook or an iPhone. Your head is the target, not the device. Knowledge equals protection with this issue, and that’s what all these words are here for. Please be aware, and cultivate a healthy mistrust for the unexpected.